Introduction to networking
Introduction to network addresses and routes
Lets consider a relatively simple home network as shown in the diagram below. This is more complex than most home networks which have an Internet router and then a single network which all devices connect to. However, this is much simpler than most corporate networks. It will aid us in explaining networks.
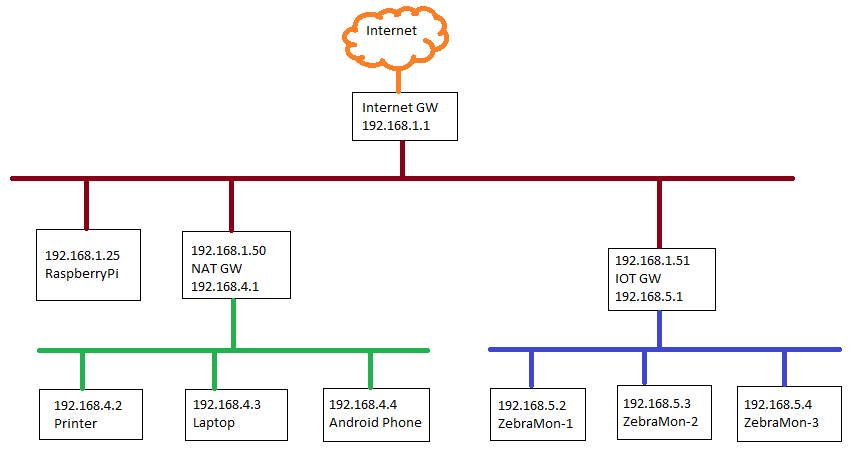
At the top there is an Internet router or modem which connects the network to the outside world. On the inside connected to the red line are devices in a "demilitarized zone", ie not quite the "outside world&quoy; and not quite the trusted "inside" either. Below that are two more networks in green and blue. These are our protected networks, and they are behind gateways which may afford them greater protection through the use of firewall rules. These red, green and blue networks will be the ones of most interest to us.
The Internet router or modem is generally implemented as a NAT gateway. NAT is network address translation. All devices should have a unique address, but we don't want to tell the outside world about our internal addresses or what these devices might be. So we hide them behind a NAT gateway. To the outside world it appears that any request from our red, green or blue networks come from the one address the Internet gateway uses to connect to the Internet Serice Provider (ISP). Each concurrent network connection is assigned a unique source port on the Internet modem, which the maintains a table of these and our internal devices and ports used to communicate.
Lets consider the addresses we are using. There are 2 types of Internet Protocol (IP) available, IPv4 and IPv6. IPv6 should be the way things have been moving to over the past 20 or so years, but IPv4 is still extremely common. IPv4 is what one is most likely to encounter, given it uses shorter 32 bit addresses means its has a simplicity which makes it popular. Each of these addresses consist of 4 bytes of 8 bits each. With each byte separated by dot. This each number in an IPv4 address can range between 0 and 255. A netmask is applied which splits the address into a network and a node portion. This is often expressed with a "/" followed by a number. Where the number will indicate how many bits at the start of the address specify the network. Therefore 192.168.4.0/24 means the first 24 bits (3 bytes) represent the netowrk number, and then remaining 8 bits (1 byte) the node on the network. This format of network address is called a Classless Internet Domain Routing (CIDR) notation. Discussing IPv4 classes is out of scope here, and is an older concept. An alternative form is to have a netmask to indicate the network portion of the address, and like the address is expressed as a set of 4 numbers each representing a byte. for the 192.168.4.0/24 network, it would have a mask of 255.255.255.0.
These addresses, and in particular the network address portion, is important here because it is what is used to distinguish between different networks and how data flows. Once connected to a network each device should have an address and be aware of its network mask. That will let the device detine if another device is on the same network as itself or if it is somewhere else. If the device (say a laptop) needs to send data to another device (say a printer) it simply places a "packet" of data on the network and off it goes. But if it needs to go elsewhere the node looks at a routing table to determine where to send the data. In our diagram lets assume we have xymon running on the Raspbery Pi (192.168.1.25) and it needs to acknowledge data sent to it from a HyraFerret decice at 192.168.5.3. The routing table on the Raspberry Pi should have an entry which effectively says, to reach 192.168.5.3 you must go via 192.168.1.51. If it cannot find this entry it will use a default route, which will probably be the Internet router 192.168.1.1. If it can't reach the HyraFerret node, it will timeout as the device is unreachable.
What though if the device the Raspberry Pi (192.168.1.25) needed to reach was hidden behind a NAT firewall? The NAT firewall will hide its protected network from the Raspberry Pi, so the acknowledge is sent to the NAT firewall as if the NAT firewall sent the orignal packet of data. The NAT firewall will then use a lookup table to find which device on its network sent the orignal request, and the NAT firewall then forwards the request back to the device. Using this it is quite possible to have multiple layers of NAT firewall forwarding data, and hiding local networks. But perhaps the Raspberry Pi wanted to send something to the printer hidden behind the NAT firewall. In this case the 192.168.1.50 address of the NAT firewall should be configure with port forwarding. It will listen to a port number (say the printer port, even though it is not a printer), and forward any network traffic reaching that port to the printer port on 192.168.4.2. On the Raspberry Pi printing would be configured as if the NAT gateway were the printer.
If devices such as Andriod table or IOS phones are connected behind the NAT device, they do not need to be aware of multiple networks attached to the DMZ network. (red in diagram) They will connect to their NAT gateway, and the NAT gateway will handle the routing from there.
What are ports? These are numbers which represent a particular application, and for our purpses could be considered as a label indicating where it should go. This could be compared to a parcel being delivered to a residential address, the address might where the parcel gets dropped off but we need to know who it is intended for. The recipient would be expected to know what to do with the contents of the parcel. A parcel containing machine parts might not make sense if opened by a small child. Nor would an email make sense if sent to a web browser. Therefore, in simple terms, ports will distiguish which application the network packet gets sent to. Port numbers less than 1024 are called "well known ports" and generally refer to commonly accessed services. However, there is no reason why a service should not listen for connections on higher numbered ports. Some well known ports are assigned as follows:
| Port Number | Service |
|---|---|
| 22 | Secure Shell (ssh) and Secure file transfer protocol (sftp) |
| 23 | Telnet (network terminal using plain text transmission) |
| 25 | Simple mail transfer protocol (smtp) |
| 53 | Domain name service (dns) |
| 80 | Hyper Text Transmission Protocol (http) |
| 443 | Hyper Text Transmission Protocol - secure (https) |
| 1984 | system monitor using xymon (some related products such as "Big Brother" and "Hobbit" have also used this port for monitoring) |
By using port numbers an administrator can configure port mapping on a NAT firewall. Here the external address listen on a port for connection requests to s service, eg printing. When a connection is made the NAT firewall forwards the request to specific address on the internal network which then remains hidden to the outside network. If the network device is acting as a router the administrator can create firewall rules which only allow certain connection types and/or permit access only from or to certain networks. Further discussion as to how these port maps and firewall rules are created is out of scope for this article and won't be discussed further here.
esp8266 based NAT Gateway
A project worth investigating if you would like a cheap NAT gateway router (<10USD), router or WIFI extender is this ESP based NAT gateway. It will allow you to setup firewalll rules using access control lists (ACLs) and can be configured as either a NAT gateway or a router.
If you implement this, remember this is a low end network device. Its access point (the wireless your devices connect to) is limited to no more than 8 clients. It throughput is limited but it may be quite adequate to support 8 IOT (Internet/Intranet Of Things) devices and some web browsing may be possible. You could also use a device such as a Linux machine as a router too, or purchase a commercially and purpose built router.
If implementing this it is highly recommended that beyond initial configuration or network testing / experimentation you harden the security on the device.
set config_access 0 set config_port 0 set web_port 0 set ssid_hidden 1 set monitor off save reset
Set up network routes
In this secion we will assume your Internet "modem" connects to a demilitarised zone on a 192.168.1.0/24 network. We will assume you have a secure network behind another router or firewall on 192.168.5.0/24.
ADSL / Fibre "modems"
This will vary from device to device, but if devices / machines on your secure networks need to access the Internet for webpages, email, name looksup or to get time, then the modem device will need a route to specify how it communicates to your secure network(s). This will vary drom device to device so see your user manual.
Windows Powershell
You'd need to run PowerShell as an administrator. The "-p" flag tells Windows this is to persist reboots.
route -p add 192.168.5.0 MASK 255.255.255.0 192.168.1.51 metric 10
Debian / Raspberry Pi
The route gets added to the interface definition in /etc/networks or under /etc/network/interfaces.d/*
source-directory /etc/network/interfaces.d
auto eth0
iface eth0 inet static
address 192.168.1.4
netmask 255.255.255.0
gateway 192.168.1.1
up route add -net 192.168.5.0 netmask 255.255.255.0 gw 192.168.1.51
What are the IDs used in Wireless LANS?
| ID | Description |
|---|---|
| SSID | This is the name of the network, and distiguishes the network from other networks which cover the same physical area. SSID = Service Set ID. |
| BSSID | This is the ID of one out of potentially many wireless repeaters which offer an Access Point with a given SSID. BSSID = Basic Service Set ID |
| ESSID | This is the collection of BSSIDs offering an SSID. Sometimes it is used interchanablely with SSID but is actually the collection of access points affering the SSID. ESSID = Extended Service Set ID |
Various articles exist to explain ssid, bssid and essid in more detail, eg Juniper Networks
Another concept sometimes encountered of wireless networks is the RSSI, or Received Signal Strength Indicator. This ranges in value from 0 to -100. The closer 0 the signal the stronger it is, the closer to -100 the more faded the signal becomes. A reading between -40 and -60 is good or strong, between -60 and around -85 is OK. Readings lower than -85 are weak. The Android "Wifi Analyzer" app can help you test your wireless signal strength in various locations.
| Thank you for visiting camelthorn.cloud | Home |